Netgear Router Password Cracker
. Lost your router’s username and? Couldn’t remember where you store it? There are two ways to and gain access to the router, the first method involves resetting the password to factory settings, while the second method uses the master key to gain access to the router. Here I tell yo second method use the master key and access the router. There are some keys are listed below read them and save to hack wifi. First reset the modem by inserting a pin in back of modem small hole for 5-10 seconds.
Hack Netgear Password. Change the default password on a NETGEAR router. This is a little xp password cracker I'm going to show you how to get and use.
- The French hacker Eloi Vanderbeken discovered the presence of a backdoor in principal models of routers including Netgear, Linksys and Cisco.
- How to Hack Netgear Router Wifi Password.Netgear router wifi password hacking trick with android app for wifi hacking and cracking. Wireless Router or simply wifi.
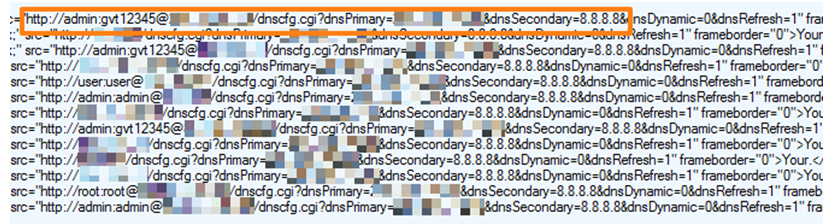
When all lights blinks collectively the modem is reset. Use the login codes given to you can set any password by logging in. Stargate trading card game. LinkedIn NetGear Router Master Key Passwords For Hacking NetGear Router Master Key Passwords For Hacking are:– Vendor Model Protocol Username Password NETGEAR RM356 Rev.
See All 183 Rows On Www.lifewire.com
NONE TELNET (none) 1234 NETGEAR WGT624 Rev. 2 HTTP admin Password NETGEAR COMCAST Rev.
COMCAST-SUPPLIED HTTP comcast 1234 NETGEAR FR314 HTTP admin Password NETGEAR MR-314 Rev. 3.26 HTTP admin 1234 NETGEAR RT314 HTTP admin Admin NETGEAR RP614 HTTP admin Password NETGEAR RP114 Rev. 3.26 TELNET (none) 1234 NETGEAR WG602 Rev. FIRMWARE VERSION 1.04.0 HTTP super 5777364 NETGEAR WG602 Rev. FIRMWARE VERSION 1.7.14 HTTP superman 21241036 NETGEAR WG602 Rev.
FIRMWARE VERSION 1.5.67 HTTP super 5777364 NETGEAR MR814 HTTP admin Password NETGEAR FVS318 HTTP admin Password NETGEAR DM602 FTP TELNET AND HTTP admin Password NETGEAR FR114P HTTP admin Password NETGEAR ME102 SNMP (none) Private NETGEAR WGR614 Rev. V4 MULTI admin Password NETGEAR RP114 Rev. 3.20-3.26 HTTP admin 1234 NETGEAR DG834G HTTP admin Password NETGEAR ROUTER/MODEM MULTI admin Password NETGEAR MR314 MULTI admin 1234 NETGEAR GSM7224 HTTP admin (none) NETGEAR ADSL MODEM DG632 Rev. V3.3.0ACX HTTP admin Password NETGEAR WGT634U HTTP admin Password NETGEAR FWG114P MULTI n/a Admin NETGEAR GS724T Rev. V1.0.11104 HTTP n/a Password NETGEAR FM114P MULTI n/a (none) NETGEAR DG834 admin Password NETGEAR WNR834 BV2 admin Password NETGEAR WNR834BV2 HTTP admin Password NETGEAR WPN824 / WPN824V2 HTTP admin Password.
He described the complete details of this Serious in above slides. After his post, other hackers around the world did further research, that shows that these devices are made by Sercomm, meaning that Cisco, Watchguard, Belkin and various others may be affected as well. The Complete List of vulnerable devices is available at his GitHub post i.e. Linksys WAG200G, Netgear DM111Pv2, Linksys WAG320N, Linksys WAG54G2, DGN1000 Netgear N150 and many more.
To see the complete list of vulnerable routers. The Python based exploit script can be downloaded from.
Update: To perform this attack, an attacker should be the part of router's network, but also there are more than 2000 vulnerable routers available on the Internet, according to Shodan Scan search i.e &.